Blogs
Milestones and updates.
The 8 layers of security your data center must have
Digital transformation has resulted in cloud service providers demanding more storage facilities to keep up with the growing volume of big data generated every year. Because a data center houses information, applications and services that businesses use every day, organizations must ensure they are using appropriate security measures to protect the facility.
In our previous blog, we highlighted the consequences of an inadequate data center security. But what are the security standards your facility should have to meet and maintain compliance? Here, we outline how SpaceDC’s 8 layers of security sets the benchmark for best practices in safeguarding your data.
“The right data center for you today must also be the right data center for you tomorrow.”
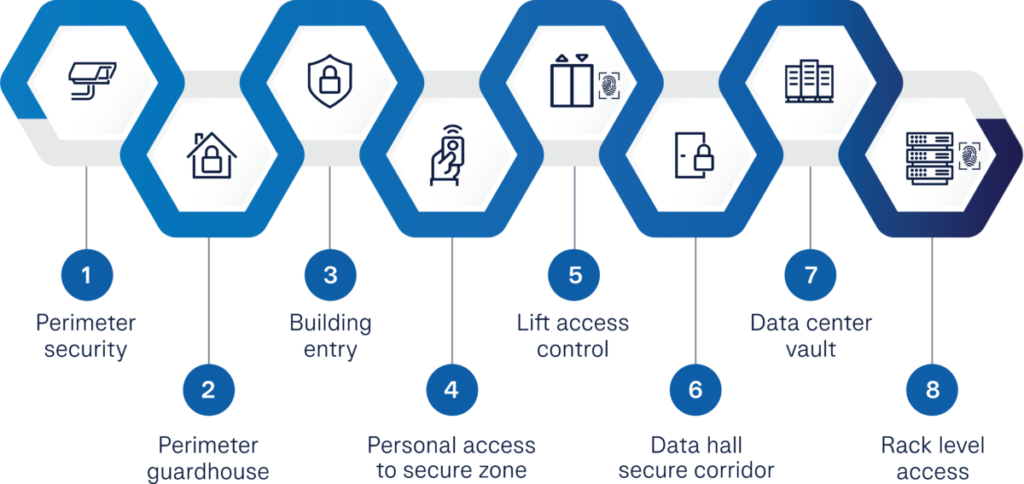
1. Perimeter security
On the outer perimeter of the data center is the multi-faceted wall, the first line of defence to withstand every possible type of attack and natural disaster. In 2017, five suspects were arrested after breaking into a data center in Johannesburg and stealing more than USD $130,000 worth of copper cables. Physical barriers are important as they serve to dishearten potential intruders. To ensure security at a maximum level, the perimeter wall needs to be coupled with additional features that we have highlighted below.
2. Perimeter guardhouse
The second layer is the guardhouse at the fence. All visitors should be required to register at least 48 hours before their visit and answer a series of security questions from the Access Request Application System regarding their background, purpose of visit and list of accompanying people. They should only be allowed access to the facility in limited zone areas after prior screening and approval.
3. Building entry
Upon entry, any items that visitors carry must be declared through an industrial x-ray and metal detector to ensure no unauthorized items are brought into the site.
4. Personal access to secure zone
Visitors to the data center should then be given access passes to specify which areas they are allowed to enter, and which areas are prohibited. Then, the visitor should pass through a small air locked room – the human trap – where they get weighed, and any large discrepancies in the visitors’ weight at the site of arrival and departure will be highlighted to security to uncover the root cause. This ensures that no item gets left behind that could potentially cripple the security of the facility.
5. Lift access control
For high rise data center buildings, visitors can move from the airlock through to the liftaccess control and should only be permitted to use their designated lifts. Visitors will only be given access to certain floors to prevent unauthorised personnel. Every person with access to the facility has the potential to undermine any of the security systems, hence limiting the movement of visitors around the facility is crucial to keeping the integrity of the data center.
6. Data hall secure corridor
Smart sensors and CCTV should be installed along the aisle to prohibit tailgating. A no tailgating policy is essential to enable the Network Operations Centre (NOC) to monitor every individual entering the data hall and beyond. This is crucial, as it ensures the accuracy of all visitor data, which would be required in the event of a security breach at the facility.
7. Data center vault
Vaults should be under comprehensive CCTV surveillance for any suspicious activity, and to maintain visual contact of every visitor at all times, as this is where the racks are housed. At any point in time, a data center must know exactly who is in the vault, where they are and what they are doing. If there are more people than there should be, an alert that should go off.
8. Rack level access
Only a very specific, pre-assessed, pre-approved selection of people will be given a biometric key to obtain access to the rack. As biometric access cannot be duplicated or physically stolen, it ensures the safety of the data housed on the racks. On top of this, many customers can opt to have their own rack surveillance based on their specific needs.
Summary
A good operations team needs to consider the worst case scenario and apply all possible security measures to ensure an impregnable facility. Following the industry standard is not enough, facilities should always be updated on new technology advancements or developments in the threat landscape and proactively anticipate them.
SpaceDC understands the importance of maintaining data security and implements the latest safety standards to keep your information intact. We set the benchmark for best practices in security innovations to create a formidable fortress against break ins and unlawful entry in the interests of your businesses.
If you would like to find out how SpaceDC ensures maximum security for our data center, read our whitepaper or contact us today.
Related blogs
Deep dive into our white papers below to read the latest industry reports on topics ranging from green facilities to data center security and digital transformation.




